The cryptocurrency frenzy that began earlier this year has drawn much attention to blockchain technology and its decentralized structure. As demonstrated by breaches from MyHeritage to Saks and Lord & Taylor in the first six months of 2018, unsecure centralized … Continue Reading
Biometrics and AI-Powered Continuous Verification
By FS INSIDER, January 17, 2018 Publised in www.financialsense.com FS Insider speaks with Deepak Dutt, CEO of Zighra, on their AI-powered continuous authentication and threat detection platform that tracks over 900 human and environmental traits to create a digital fingerprint … Continue Reading
How close are we to merging AI and blockchain?
In a digital environment where most data is siloed, there is no real incentive to share it. As a result, corporations are hoarding tons of consumer data (i.e. Google, Facebook, Alibaba, Baidu). Currently, artificial intelligence (AI) platforms help to concentrate … Continue Reading
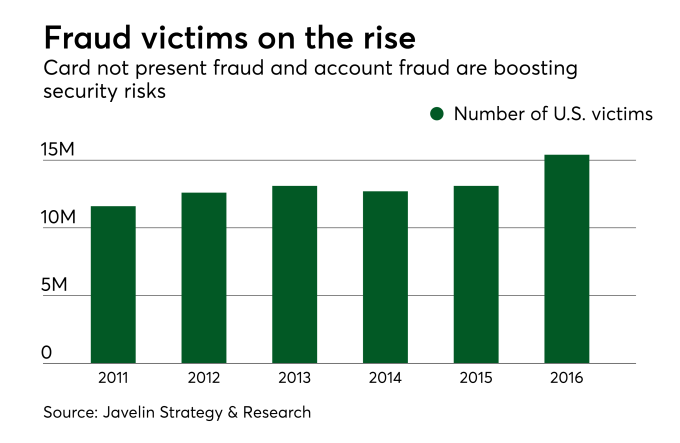
PINs, passwords and fingerprints aren’t as safe as you think
New research reveals that retailers could lose nearly $71 billion in the next five years on transactions, such as online or mobile, where the card is not present. PINs, passwords and even fingerprints are no longer a sufficient means of … Continue Reading

AMAZON GO – FRICTIONLESS COMMERCE, MOBILE FRAUD AND BEHAVIORAL BIOMETRICS?
Amazon has described Amazon Go as “a new kind of store with no checkout required”, which essentially means that you won’t have to stand in line to make payments. The Go store works with the new Amazon mobile app that … Continue Reading
AI AND MACHINE LEARNING FIGHTING MOBILE FRAUD
A recent study from LexisNexis indicates that fraud is a growing problem for online retailers, specifically the ones that offer customers a mobile commerce option. “Merchants are challenged on various fronts, including an increased volume of successful fraud attempts, a … Continue Reading

ADAPTIVE BEHAVIORAL AUTHENTICATION IN THE ENTERPRISE
Adaptive authentication involves combining multiple authentication methods to provide the ideal compromise between convenience, security, and costs. This is more contextual in nature and rely on a more implicit form of authentication based on user sessions as opposed to explicit … Continue Reading
