On November 2022, the U.S. Department of Defense published information regarding plans to shift its network to a “zero trust architecture” by 2027. In this Zero Trust Strategy and Roadmap document, the federal defense agency shared its goals about what it aims to achieve and what its vision is for the future: implementing stronger defenses against cyber attacks via a dynamic and adaptive approach (zero trust).
“What we’re aiming for by 2027 is to have zero trust deployed across a majority of our enterprise systems. That’s an ambitious goal, but the adversary capability we’re facing leaves us no choice but to move at that pace.” – John Sherman, CIO, DoD.
Zero trust touches everything relating to the IT ecosystem and everything that goes on in the background. It promotes the idea that there are no traditional network boundaries; organizational assets and resources can be anywhere — on prem, in the cloud, or a mix of both. This makes it a versatile approach to hardening organizational cyber defenses. Therefore, everyone with access to an organization’s network or IT resources must have their identities continuously vetted throughout their connections.
To help federal bodies and contractors align with the enterprise-wide strategy, on November 15, 2022, DoD put forward a Zero Trust Capability Execution Roadmap, which establishes baseline capabilities and activities to achieve target and advanced Zero Trust levels, on each of the strategy’s seven pillars.
3 Key factors in Successful DoD Zero Trust Implementation
As the DoD is working hard to be a leader in Zero Trust adoption among the federal government and its contractors, their plan will, of course, need some adjustments and may not be a perfect fit for everyone. However, there are 3 key paths for the successful implementation of the strategy within any organization:
- Workforce zero trust – this is about ensuring that only authorized users and, respectively, only authorized secure devices gain access to enterprise applications, networks, and systems, regardless of the user’s location. One strong way to achieve this is by deploying continuous authentication across all corporate or government-owned devices to ensure that only the people you trust, such as employees, contractors, partners, or vendors, are accessing your data.
- Workloads zero trust – this focuses on safe access and protecting workloads as they move through cloud environments. Strong security practices are key, especially when an application’s database is accessed via an API, microservice, or container that operates in virtualized contexts, such as private clouds.
- Workplace zero trust – this concentrates on secure access for all devices, including Internet of Things (IoT) devices, that connect to business networks, including but not limited to: user endpoints, physical and virtual servers, printers, cameras, HVAC systems, kiosks, and Industrial control systems (ICS) among others.
The 7 Pillars of Zero Trust
The 7 pillars of zero trust highlighted within the U.S. Department of Defense (DoD) help categorize the capabilities and technologies required to perform Zero Trust functions. These 7 pillars are associated with an interconnected group of strategic resources which are bound together in a Zero Trust Framework. The following diagram shows the 7 zero trust pillars in addition to Continuous Authentication and Digital Identity based Verifiable Credentials.
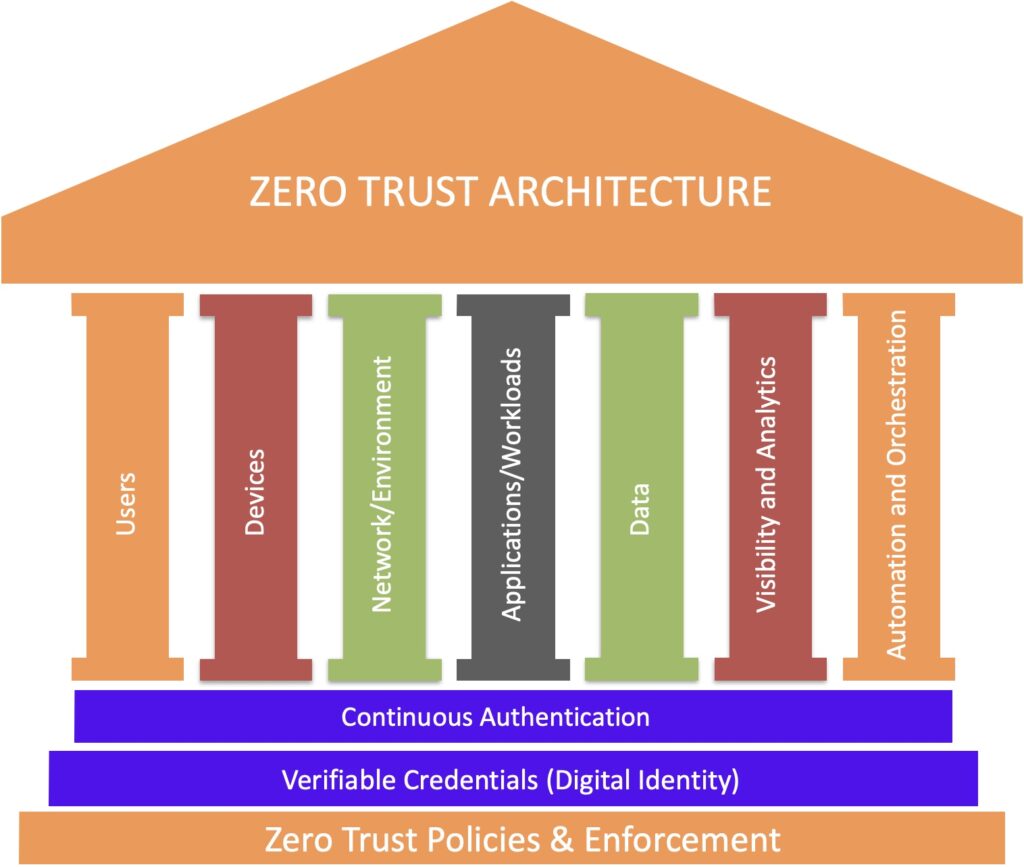
- Users: Organizations need the ability to continuously authenticate, authorize, and monitor activity patterns to govern users’ access and privileges while protecting and securing all interactions.
- Devices: Use of device digital identity (e.g., TPMs – Trusted Platform Modules) to authenticate access in real time. Devices must also be patched to mitigate vulnerabilities.
- Network/Environment: Segmentation, isolation, and policy restrictions are three critical components to control access and manage how data moves on your network. This approach helps to restrict access and prevent lateral movement within the network.
- Applications and Workloads: Whether using resources that are on-premise, cloud, or a hybrid approach, the idea here is to secure the application layer.
- Data: Secure organizational data by developing a comprehensive data management strategy and integrating data security measures such as at-rest and in-transit data encryption. This will help protect data both while it’s on servers or moving between two endpoints.
- Visibility and Analytics: Having full visibility of the IT environment is crucial to keeping it secure. One can’t protect assets one doesn’t know exist, and can’t stop attackers when one doesn’t realize something is wrong. Organizations can gain actionable insights to improve cyber security by analyzing network’s traffic and user behaviors in real time to identify threats. Just be sure to consider that some traffic may contain sensitive data, so decide the best approach (such as informing users and obtaining their consent ahead of time).
- Automation and Orchestration: Automation is a scalable approach that takes monotonous tasks off administrators, freeing them up to focus on tasks that require critical thought processes. These tools also enable you to quickly sort through all the noise your security tools generate to find valuable data.
Access Controls and Access Management Are Critical to an Organization’s Cyber Defences
Zero trust as a cyber security approach has gained strong momentum over the past several years, partly because of the requirements around identity-based authentication and user authorization. Access controls and management play together to boost organizational cyber security:
- Access controls: the rules, settings, and tools used to control access to sensitive data and resources.
- Access management: the process of setting up and managing who has authorization to access specific resources and systems.
Neither of these is foolproof and requires another critical security layer in the form of authentication. User and device authentication are all about ensuring that only entities (e.g., those whose digital identities have been verified and their authorizations confirmed) can access your secure digital assets.
Continuous Authentication is Integral to the DoD Zero Trust Strategy
A key element of the zero trust approach is a concept known as continuous authentication. Under “User,” the first pillar of the DoD strategy, it’s explained that one should never trust a user, even after they have first logged in to a system using their credentials. That a user should still be viewed as a potential threat throughout their entire interaction with a network.
The idea behind continuous authentication is that all network users, including your employees, must not only prove their identities when they first log in but also continuously prove their identities throughout their sessions.
The rationale is that, because session IDs can be set to last for extended periods – anywhere from a few hours to even a few weeks. This means that if a hacker steals an authenticated user’s access tokens (session IDs and cookies), they can pretend to be them and access whatever protected resources their account has the authorization to access.
It’s true that you can set timeout limits to take effect after every few seconds, but constantly bothering the user all the time will lead to user frustration and loss of productivity and even the user giving up on using the system.
A key component of any continuous authentication approach is behavioural biometrics, which involves “observing activities of users, information systems, and processes and measuring the activities against organizational policies and rules, baselines of normal activity, thresholds, and trends.” This approach can help continuously and passively verify user identity without frustrating the user.
Continuous Authentication requires Verifiable Digital Identity
For zero trust security to work, user’s need to have a way to prove that they are the real user and not an imposter who’s trying to fraudulently access sensitive data, systems, and other resources. One way to achieve this level of reliable and verifiable digital identity is by leveraging public key infrastructure (PKI).
In a zero-trust environment, there are no implicitly or explicitly trusted users, devices, or zones within an organizations network or IT environment. The digital identities of everything and everyone must be authenticated continuously using verifiable methods. PKI based tools including digital certificates are a means of achieving precisely that. Verifiable credentials enable trusted third parties to attest to a digital identity’s authenticity.
The case for Continuous Multi-Factor Authentication (CMFA) & Compliance
The US DoD zero trust strategy provides agencies with the flexibility to look for a more modern way to authenticate users through new technology like Zighra’s Continuous MFA. Zighra is the world’s first FIDO certified behavioural authentication solution. Zighra’s unique, machine learning powered behavioral biometric and continuous MFA solution provides the highest fidelity authentication, aligning well with NIST 800-63B Authenticator Assurance Level 3 (AAL3) requirements.
While device signals, machine learning and phishing-resistant MFA are not the only requirements defined in the Federal Zero Trust Strategy, these are ones that Zighra uniquely solves with its patented Continuous MFA solution. Removing shared secrets involved in the entire process, leaves nothing to phish or intercept. Moreover, the Zighra passive machine learning approach means that one can integrate the strongest MFA quickly and consistently across applications and platforms.
Explainable AI
Current state of the art AI systems are based on neural networks that operate as black boxes. However, the effectiveness of these systems is limited by the machine’s current inability to explain their decisions and actions to human users.
The Zighra solution provides novel automated, real-time situational awareness and triage of behavioural compromise alerts using explainable AI/ML. This will dramatically increase security analyst effectiveness and efficiency and dramatically reduce the risks and costs of attacks. Our patented method leverages real-time, fine-grained knowledge of the real user behaviour and the system processes they are legitimately using to discover threat behaviour that is using their credentials but cannot be attributed to the real user.
It allows Security Officers and analysts to immediately be alerted of any anomalies and know whether they are interacting with their departmental users. Furthermore, the platform provides a visual explainable AI/ML interface that explains the rationale of why the system made specific decisions and insights into the models. These models can further be tuned to improve the performance and future decision making capabilities.
Zighra’s explainable AI/ML capability helps cybersecurity analysts in the security operations center (SOC) as well as information management (IM) teams to strategically improve the speed and accuracy of cyber incident alerts and resolution while enabling the effective and ethical use of AI.
