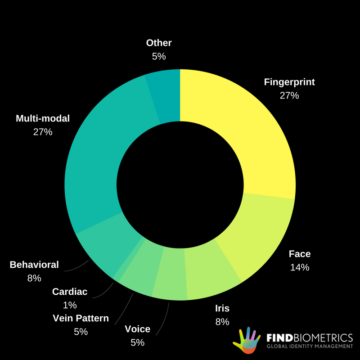
2017 – The Year of Behavioral Biometrics? 2016 has been a challenging year for politics, public sanity and celebrity longevity, but also, for individuals and companies, a testing time in terms of online security. Fighting against increasingly sophisticated and targeted … Continue Reading

AMAZON GO – FRICTIONLESS COMMERCE, MOBILE FRAUD AND BEHAVIORAL BIOMETRICS?
Amazon has described Amazon Go as “a new kind of store with no checkout required”, which essentially means that you won’t have to stand in line to make payments. The Go store works with the new Amazon mobile app that … Continue Reading

AI AND MACHINE LEARNING FIGHTING MOBILE FRAUD
A recent study from LexisNexis indicates that fraud is a growing problem for online retailers, specifically the ones that offer customers a mobile commerce option. “Merchants are challenged on various fronts, including an increased volume of successful fraud attempts, a … Continue Reading
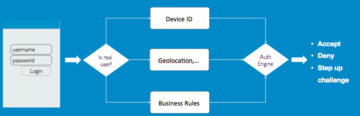
ADAPTIVE BEHAVIORAL AUTHENTICATION IN THE ENTERPRISE
Adaptive authentication involves combining multiple authentication methods to provide the ideal compromise between convenience, security, and costs. This is more contextual in nature and rely on a more implicit form of authentication based on user sessions as opposed to explicit … Continue Reading

COMPANIES MOVE BEYOND PASSWORDS WITH HUMAN BEHAVIOR ALGORITHMS
Great mention of Zighra in the CIO Journal from WSJ on Zighra’s role in behavioral authentication within the enterprise – Read more
GOOGLE SHOWCASES BEHAVIORAL BIOMETRICS AT IO
Behavioral biometrics or behaviometrics is a form of biometric authentication that has shown promise to address the continuous frictionless authentication problem by allowing the device to identify the user without the user doing any explicit authentication actions while providing a … Continue Reading

ADAPTIVE BEHAVIORAL BIOMETRICS A CRITICAL SECURITY LAYER
We are on the cusp of a global shift to change how we identify the individual. Smart devices including mobile phones, wearables and global access to cellular services have pushed biometrics as the new paradigm in user authentication and security … Continue Reading
CAN ADAPTIVE BIOMETRICS THWART DATA BREACHES?
In a recent study, CNN Money reported that 317 million types of malware were released into cyberspace last year. This translates to nearly a million new (or variants) malware every day. The article also reported that whenever a new attack was released, … Continue Reading

WHY ADOPT BEHAVIORAL BIOMETRICS AS PART OF YOUR MULTI-MODAL STRATEGY
The next wave in biometric security is predicted to be the use of multiple biometric authentication systems for human identification. Multi-modal biometric authentication systems take input from a single or multiple biometric sensors for measurement of two or more different biometric characteristics to … Continue Reading

HACKERS GET ACCESS TO SAMSUNG PHONES VIA MOBILE SECURITY FLAW
Mobile security researchers have discovered a security flaw in Samsung’s default keyboard on its smartphones which can be exploited by hackers to snoop around your phone. Hackers could potentially access the phone’s camera, read text messages, install apps and use the microphone to … Continue Reading