
While cleaning up my spam folder, I noticed an email from Amazon.com with the subject title “ You just need to confirm your account”. Before deleting the email, I clicked on it to make sure I was not deleting a legit message from Amazon. Thankfully, today’s spam tools are smart enough to flag fraudulent messages if the “from” email (official@ail.com) doesn’t come from Amazon, so I could safely delete the message.
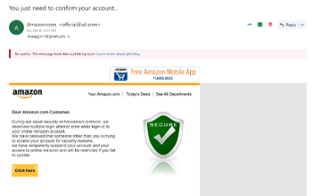
This is just one example of social engineering where fraudsters use well known brands to trick users into giving their login information. It is one of the hardest forms of attack to fight as users are actively involved in the process. They do not notice what is wrong at the time, only to discover unusual activities on their account weeks or months later.
On mobile devices, these attacks are even more common today. Fraudsters mimic the interface of popular apps to steal usernames and passwords. Despite an increased interest in cybersecurity threats, users are still easily tricked by increasingly effective and persuasive means. Try to spot what is wrong with this recent fraudster phishing login page:
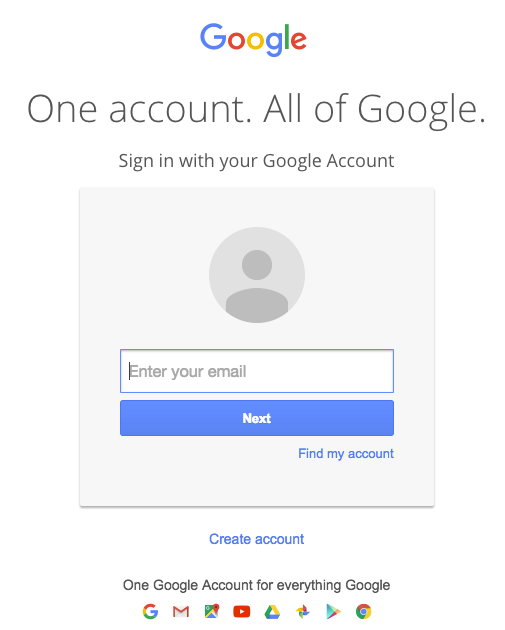
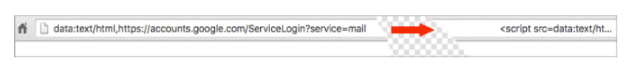
You simply can’t see what is wrong, because it is a perfect copy. Except it is not from Google. The only way anyone would identify that something is wrong would be to inspect at the browser address bar and see the URL prefix was “data:text/html,” rather than the the normal “https://accounts.google.com/…”. What was really loaded was not a web page but instead a script that generated the fake login page and acquired the user’s account credentials.
Social engineering attacks like these are now used in over 66% of all successful attacks by hackers, hacktivists and nation states. Last year, according to Agari’s Email Security: Social Engineering Report, 60% of enterprises were victims of social engineering attacks, 65% percent of these compromised employee authentication credentials and 17% breached financial accounts. Enterprise bring your own device (BYOD) policies increase both the opportunities for these attacks and the difficulty in stopping them.
A form of social engineering usually involves the following three steps. The user receives a notification from the attacker claiming to be a support person working for a trusted brand. Then, the fraudster manages to convince the user to install a remote support tool on the user’s mobile device. Last but not least, the user is asked to grant remote access to the mobile app to reproduce the problem. From there, the fraudster can “run tests” on the app to help the user and make his case without the user noticing.
Social engineering is one of the core security problems that can be addressed by behavioral biometrics. Beyond just securing the device, Zighra’s behavioral biometric solution flags account takeovers by continually authenticating the real user integrating with the app. This powerful ability to sense the account is being accessed by the real user interacting with the device, and that it is a good device, effectively helps in the fight against bad bots and fraudsters.
