With mobile fraud on the rise and the cyber world becoming a dangerous place for the uninitiated to wander around in, businesses relying on ecommerce and virtual transactions have a responsibility to ensure their less experienced customers are adequately protected. Traditional methods of identifying approved users and granting access are under attack, and a better solution is urgently needed.
Vulnerability of Existing Authentication Methods
It’s painfully clear that existing methods of mobile security are inadequate, with passwords rapidly becoming extinct. Two-factor authentication (2FA) based on text-delivered codes offered a sense of security for a period, but this 2017 publication from the National Institute of Technology indicates 2FA is no longer part of their recommended protocols. Even multi-factor authentication (MFA) is proving insufficient protection against determined fraudsters, and the more layers of protection that are added the greater the inconvenience to the user. This situation has resulted in a social and technological imperative to develop better solutions, and n-dimensional authentication is the response.
What N-Dimensional Security Means
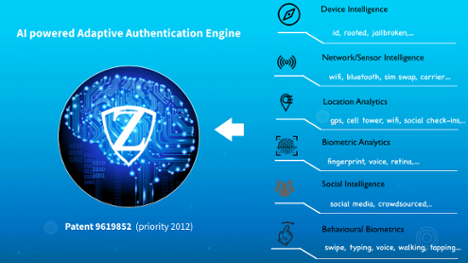
In mathematics, the n-dimension essentially refers to an unknown variable. In terms of behavioral biometrics, however, we’ve adapted its use to refer to “all” or “multi” dimensional. When a range of dimensions are applied to authentication solutions, it takes user security to a new level of efficiency. N-dimensional authentication uses all possible degrees of intelligence, including:
- Human-machine interactions
- Device intelligence
- Network intelligence
- Social intelligence
- Location intelligence
- Biometric intelligence, based on facial recognition, fingerprinting and other physical attributes
- Behavioral intelligence, such as muscle memory, cognition and habits.
When these layers are aligned with each other and seamless cross-referencing takes place without active user involvement, we achieve a much higher standard of security than has ever been possible before.
Adding Machine Learning Benefits
One of the factors making n-dimensional authentication effective is the ability to include sophisticated machine learning in security protocols. Instead of relying on methods that are proved to be vulnerable, this technique uses mathematics and science to find and evaluate the strongest behavioral data points. The system then uses these to automatically construct adaptive and continuous authentication processes, which protect the user from the point of login throughout his or her journey completing transactions and through logout.
Using Behavioral Patterns as a Denominator
Many of these layers are already in use for authentication purposes as point systems, but the addition of behavioral intelligence enables mobile devices to be so attuned to their users so that “how” we interact becomes the password. The way we walk, the angle at which we hold a smartphone, and the speed of typing all offer unique identifying characteristics. Combined with the other n-dimensional elements, the user’s picture is unassailably specific.
Over time, this type of authentication may well come to include “brainprints”, which are readings of how a person’s brain reacts to certain words or tasks. This method has been shown to have a 98 percent accuracy in identifying one person among a group of more than 100. Given that fingerprint accuracy is 99.8 percent, this will make a useful additional layer of security to the n-dimensional protection process.
An Unbreakable Layer of Protection
With every new technological achievement comes a new series of threats. Protection levels need to be accurate, intuitive, multi-faceted and frictionless to enable users to focus on living their lives and conducting their business, rather than protecting their identities and financial profiles. N-dimensional authentication offers the opportunity for ongoing development and the incorporation of additional authentication factors to eventually create what we hope will be an unbreakable layer of protection.
Learn more about Zighra’s solutions in this space and how our recently granted patent provide true N-dimensional authentication to cotinuously protect users and data.
