Back in 2012, I was trying to deploy security certificates on old mobile handsets. Nobody wanted to use them. Security had become so cumbersome that it was defeating its own purpose. That frustration sparked a question that would reshape our … Continue Reading
Security

Sovereignty Through Innovation: Why Canada Must Lead the Next Era of Defence Technology
After years of deploying AI-based cybersecurity and fraud detection systems across global markets — from London and New York to Silicon Valley, Hong Kong, and the Middle East — I saw firsthand how nations prioritize sovereign control over their critical … Continue Reading

From Battlefield to Arctic: First Principles Thinking is Critical to AI and Drone Defence Innovation
The future of warfare is transforming before our eyes. As I witnessed at a recent defence and security conference, traditional military procurement strategies are being upended by the rapid evolution of AI and drone technology. The lesson from active conflicts … Continue Reading

The Growing Threat of GPS Jamming in Canada: The Need for a National Detection System
Canada’s reliance on GPS and GNSS for critical infrastructure, defense, and economic operations is growing—but so are the threats of jamming and spoofing. As adversarial nations test electronic warfare capabilities, Canada remains without a coordinated national strategy to detect and mitigate these risks. With billions of dollars at stake, investing in GNSS protection is no longer optional—it’s essential. … Continue Reading
Explainable AI: The Key to Unlocking Generative AI’s Potential
In a world increasingly captivated and transformed by artificial intelligence, the roles of Generative AI and Explainable AI have become pivotal. Yet, their true potential is unleashed only when these two powerful forces intersect. We aim to explore this crucial … Continue Reading
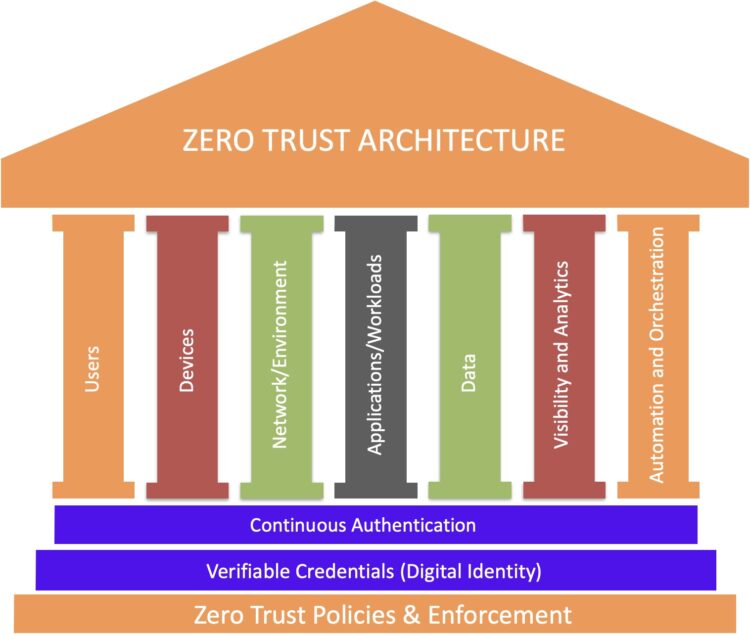
Continuous MFA powered by Explainable AI & the Zero Trust Journey
On November 2022, the U.S. Department of Defense published information regarding plans to shift its network to a “zero trust architecture” by 2027. In this Zero Trust Strategy and Roadmap document, the federal defense agency shared its goals about what … Continue Reading

Zighra Secures Canadian Coast Guard Contract to Pilot Explainable AI Solution for Enhanced Cybersecurity
Zighra Successfully Qualifies to Sell Directly to Government of Canada under Pathway to Commercialization Program … Continue Reading

Zighra Successfully Qualifies to Sell Directly to Government of Canada under Pathway to Commercialization Program
Zighra Successfully Qualifies to Sell Directly to Government of Canada under Pathway to Commercialization Program … Continue Reading
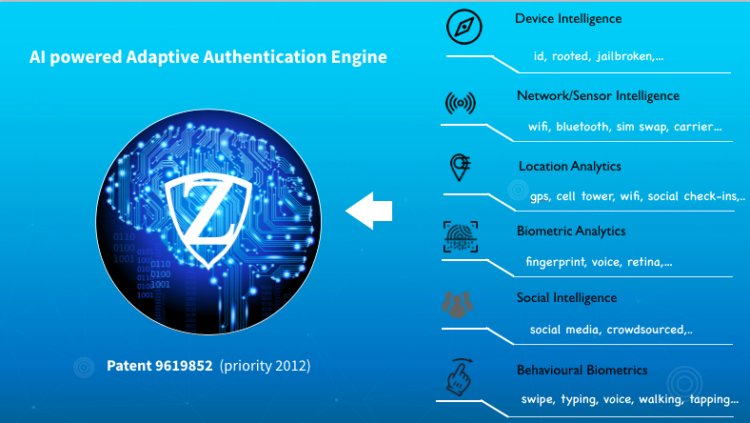
N-dimensional Authentication Takes Behavioral Biometrics to New Levels
With mobile fraud on the rise and the cyber world becoming a dangerous place for the uninitiated to wander around in, businesses relying on ecommerce and virtual transactions have a responsibility to ensure their less experienced customers are adequately protected. Traditional … Continue Reading

ADAPTIVE BEHAVIORAL BIOMETRICS A CRITICAL SECURITY LAYER
We are on the cusp of a global shift to change how we identify the individual. Smart devices including mobile phones, wearables and global access to cellular services have pushed biometrics as the new paradigm in user authentication and security … Continue Reading
